Introduction
Welcome to the cosmos of Amazon Web Services (AWS), where the stellar Virtual Private Clouds (VPCs) serve as the blueprint for your cloud architecture. In this extensive guide, we embark on a comprehensive journey through the realms of AWS VPC, exploring its multifaceted components, avant-garde features, and practical applications. So, fasten your seatbelts as we unravel the intricacies of VPC peering, transitive connectivity, and the game-changing VPC endpoints that define the AWS galaxy. 🌌
In Amazon Web Services (AWS), a Virtual Private Cloud (VPC) is a virtual network dedicated to your AWS account. It provides a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. When you create a VPC, you can select its IP address range, create subnets, and configure route tables, network gateways, and security settings.
Understanding the Building Blocks: Decoding AWS VPC
At the core of your AWS infrastructure lies the VPC, a virtual haven for your cloud resources. Let's take a plunge into the fundamental components that shape the AWS VPC landscape.
1. CIDR Block: The Galactic Address of Your VPC
When you create a VPC, you must specify a range of IPv4 addresses for the VPC in the form of a CIDR block. This block defines the range of IP addresses available for your VPC. It's important to choose a CIDR block that is large enough to accommodate your resources but not excessively large to avoid wastage of IP addresses.
2. Subnets: Realms of Order and Isolation
A subnet is a range of IP addresses in your VPC. You divide the CIDR block of your VPC into one or more subnets. Each subnet must be associated with an availability zone, and instances within the subnet can communicate with each other. Subnets provide a way to organize and isolate resources within the VPC.
3. Internet Gateway: The Cosmic Gateway to Connectivity
An Internet Gateway enables communication between instances in your VPC and the Internet. It allows instances to have public IP addresses and connect to the internet for tasks like downloading software updates or interacting with external services. Each VPC can have at most one Internet Gateway.
4. Route Tables: Navigational Charts for Network Traffic
A route table contains a set of rules, called routes, that are used to determine where network traffic is directed. Each subnet in a VPC must be associated with a route table, which controls the traffic flow for the subnet. Route tables are used to specify the routes for traffic within the VPC and to external networks.
5. Security Groups and Network ACLs: Guardians of the Cosmic Realm
Security Groups act as virtual firewalls for your instances. They control inbound and outbound traffic at the instance level. You can define rules to allow or deny traffic based on protocols, ports, and IP addresses. Security Groups are associated with instances and provide an additional layer of security.
Elevating Your VPC Game: Advanced Features Unveiled
VPC Peering: Forging Cosmic Connections
VPC peering allows you to connect one VPC with another in the same or different AWS accounts. Peering enables the exchange of traffic between instances in the peered VPCs as if they are on the same network. It does not require the traffic to traverse the internet. 🌐
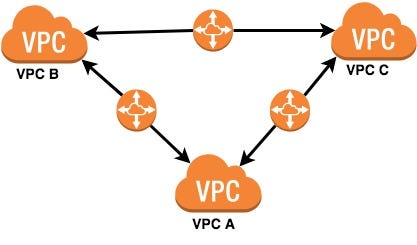
VPC peering is a networking connection between two Virtual Private Clouds (VPCs) in Amazon Web Services (AWS) that allows them to communicate with each other as if they were on the same network. VPC peering enables the exchange of traffic between instances in the peered VPCs using private IP addresses, without the need for internet gateways, VPN connections, or Direct Connect.
Here's a detailed explanation of VPC peering with an example:
VPC Peering Components:
Requester VPC: The VPC that initiates the peering connection is called the requester VPC.
Accepter VPC: The VPC that accepts the peering connection is called the accepter VPC.
Peering Connection: The connection itself, which is established between the requester and accepter VPCs.
Example Scenario:
Let's consider a scenario with two VPCs: VPC-A and VPC-B.
Step 1: Create a VPC in each AWS Account
In Account A:
CIDR Block: 10.0.0.0/16
Subnets: Private subnet (10.0.1.0/24), Public subnet (10.0.2.0/24)
In Account B:
CIDR Block: 192.168.0.0/16
Subnets: Private subnet (192.168.1.0/24), Public subnet (192.168.2.0/24)
Step 2: Create a VPC Peering Connection
In the AWS Management Console for Account A, initiate a request to peer VPC-A with VPC-B.
Specify the Account ID of the owner of VPC-B.
AWS will generate a unique VPC peering connection ID.
Step 3: Accept the VPC Peering Connection
- In the AWS Management Console for Account B, accept the VPC peering connection request from Account A.
Step 4: Update Route Tables
In both VPC-A and VPC-B, update the route tables to include routes for the CIDR blocks of the peered VPC.
In VPC-A route table, add a route for 192.168.0.0/16 with the VPC-B peering connection ID as the target.
In VPC-B route table, add a route for 10.0.0.0/16 with the VPC-A peering connection ID as the target.
Step 5: Security Group and Network ACL Rules
- Ensure that the security groups and network ACLs in both VPCs allow the necessary traffic for communication between instances.
Step 6: Verify Connectivity
Launch instances in the private subnets of both VPCs.
Instances in VPC-A should be able to communicate with instances in VPC-B using private IP addresses.
Considerations:
VPC peering is not transitive. If VPC-A is peered with VPC-B and VPC-B is peered with VPC-C, VPC-A and VPC-C are not automatically peered.
CIDR blocks of peered VPCs must not overlap.
Ensure that route tables, security groups, and network ACLs allow the necessary traffic.
VPC peering connections can be established between VPCs in the same AWS account or different AWS accounts.
VPC peering is a powerful feature that facilitates communication and resource sharing between different VPCs, making it easier to design and deploy multi-tiered applications, collaborate across projects, or implement network segmentation.
Transitive Connectivity: Crafting Hub-and-Spoke Brilliance
While VPC peering remains non-transitive, the astute architect can achieve transitive-like connectivity through a hub-and-spoke topology. Imagine building cosmic bridges between islands in the AWS archipelago. 🏝️
Example:
VPC-A connects to VPC-B, and VPC-B connects to VPC-C. Instances in A can indirectly communicate with instances in C via B.
VPC Endpoints: Secure Portals to AWS Services
VPC endpoints emerge as secure portals, allowing private connections to AWS services sans the public internet traverse. It's akin to possessing a secret passageway to AWS resources, enhancing both security and efficiency. 🔐
A Gateway Endpoint is a VPC endpoint that allows your VPC to connect to AWS services using a direct connection through your VPC's internet gateway. Currently, the only supported service for Gateway Endpoints is Amazon S3.
Example: Amazon S3 Gateway Endpoint
Suppose you want to allow instances in your VPC to access Amazon S3 using a Gateway Endpoint.
Steps:
Create an S3 Gateway Endpoint:
- Specify your VPC when creating the Gateway Endpoint for S3.
Update Route Tables:
- Update the route table associated with your subnet to include a route pointing to the S3 Gateway Endpoint.
Access S3 Privately:
- Instances in your VPC can now access S3 using the Gateway Endpoint, and the traffic doesn't go over the internet.
Considerations:
Security Groups and Network ACLs: Ensure that security groups and network ACLs allow the necessary traffic for communication through the VPC endpoint.
Endpoint Policies: Some services allow you to control access to the endpoint using endpoint policies. These policies specify the permissions allowed for traffic through the endpoint.
Costs: While VPC endpoints can enhance security and performance, it's essential to be aware of any associated costs, such as data transfer costs.
VPC endpoints are particularly beneficial for scenarios where security and data privacy are top priorities, as they eliminate the need for internet exposure when accessing certain AWS services.
Example Scenario:
Craft an S3 Interface Endpoint to forge a private connection between your VPC and Amazon S3. Instances can securely access S3 without exposing traffic to the vast internet.
Strategies and Reflections: Best Practices Unveiled
Default VPC:
Explanation: When you create an AWS account, a default VPC is automatically created in each AWS region. The default VPC is pre-configured with a specific CIDR block, subnets, route tables, security groups, and network ACLs. Instances launched into the default VPC receive both public and private IP addresses. It is designed to make it easy for users to start deploying instances without having to explicitly configure a VPC.
Key Characteristics:
Public and private subnets in each Availability Zone.
Internet Gateway is attached, allowing instances to connect to the internet.
Instances in the default VPC receive public IP addresses by default.
Default security group and network ACL are created.
Considerations: While the default VPC is convenient for getting started quickly, some users prefer to create custom VPCs for better control and security. Overreliance on the default VPC might lead to unintended security risks, especially if resources are inadvertently made publicly accessible.
Custom VPC:
Explanation: A custom VPC is one that you create, configure, and manage according to your specific needs. This allows you to define your CIDR block, create subnets, configure route tables, and establish security settings from scratch. Custom VPCs offer greater flexibility and control over your network architecture.
Key Characteristics:
You define the CIDR block for the VPC.
You create and configure subnets based on your requirements.
You have control over the route tables and can define custom routes.
Security Groups and Network ACLs need to be explicitly created.
You can set up VPC peering connections with other VPCs.
Considerations: Custom VPCs are often recommended for production environments and complex architectures. They allow for a tailored network design that aligns with specific security and compliance requirements. Custom VPCs are also suitable for scenarios where multiple VPCs need to be interconnected.
Conclusion✨: Your Cosmic Odyssey Begins
Armed with this interstellar guide, you are poised to navigate the expansive cosmos of AWS VPC with confidence. Whether securing your cosmic fortress through VPC peering, constructing hub-and-spoke constellations, or establishing private connections through VPC endpoints, your journey through the AWS galaxy is destined for success. 🚀 Embrace the power of AWS VPC, and let your cosmic odyssey commence!